Microsoft Defender setup, sync and overbuild#
Microsoft
Automate provides a consolidated view and management of the Microsoft Defender suite, including the partitioning of and role-based access to MS tenant data.
To enable and use MS Defender in Automate, the following steps and activities are available:
Setup#
Enable MS Defender for Office and/or Endpoint in the Global Settings.
See Global SettingsThis will also by default enable a new Microsoft Defender administrator menu item containing links to related dashboards - to easily manage the enabled items. For details, see the MS Defender management topic below.
Configure a Microsoft tenant in Automate.
This configuration will sync MS Defender data to Automate. Refer to the collection and and sync details below.
See Microsoft tenant setup
Data collection and sync#
When a tenant configuration for MS Defender is saved, Automate will:
Create a data collection instance in Automate that is then synced from the tenant.
For the data collection, if a MS Defender for Endpoint instance is added to the model called
data/DataCollection, its name is of the format: Defender for Endpoint Data Collection <hierarchy name> and collects all instances from the tenant for the following models in a batch:device/msgraphsecurity/SecureScoredevice/msgraphsecurity/Alertdevice/msgraphsecurity/Incidentdevice/mssecurity/Machinedevice/mssecurity/MachineActiondevice/mssecurity/ExposureScoreByMachineGroups
Sync MS Defender collection data to Automate and create sync schedules.
MS Defender data is synced to the tenant hierarchy.
For the schedules, these are created (according to Global Settings enabled MS Defender suite items) and by default run every 30 minutes. The schedules can sync data according to the relevant created collection and a batch sync of data takes place.
For the schedule instance, the Resource Type of the created schedule is
data/DataCollection, while the selected Resource naming format is:Defender for Endpoint Data Collection <hierarchy name>
Defender for Office Data Collection <hierarchy name>
The collected data at the tenant hierarchy is then also available when Overbuild for Microsoft is run to partition and move the data to the relevant sites in Automate.
See Overbuild for MicrosoftNote
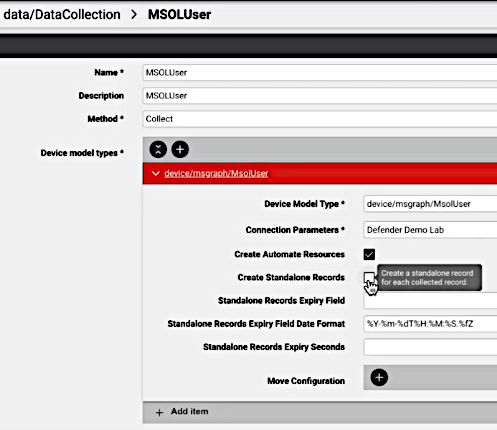
The default MSOLUser data collection does not apply the setting: Create Standalone Records, since this collection is used only for the Insights database in order to provide time series data for trends and charting.
Overbuild#
Automate’s Overbuild for Microsoft allows for the partitioning of the synced MS Defender data to relevant sites in Automate.
In particular, this includes: incident alerts, quarantine messages and MS Defender policies. The data partitioning is done according to the Model Filter Criteria (MFC) created during tenant setup.
For details on Microsoft Defender for Office and Endpoint overbuild, see: Overbuild with Microsoft Defender - by Model Filter Criteria.
MS Defender management#
MS Defender data is the can be viewed and accessed in Automate from dashboards, allowing for further analysis as well as management from policy, incident and alert management interfaces.
See:
