Microsoft Defender for Office security management and policies#
Microsoft
Overview#
Automate provides support for Microsoft Defender for Office that addresses email security threats.
In particular, Automate supports:
the rapid data sync of a large volume of quarantine messages
hierarchy-specific data management
the management of email quarantine messages, Safe Attachment Policies, Safe Link Policies
request staging areas for quarantine email messages and for requests to create and update of policies
Requests can then have the State that can be managed during the request cycle:
PENDING
REJECTED
APPROVED
COMPLETED
the management of policy configuration templates, allowing for customization
Note
The following entry under Global settings, Enabled Services needs to be enabled: Enable Defender for Office - see: Global settings.
For further setup and configuration, see: Microsoft Defender setup, sync and overbuild.
Dashboards#
The administrator interface provides dashboards for the view and management of data:
For details, also see:
- Security Management - Defender for Office Overview
- Security Management - Defender for Office Actions
By default:
The Defender for Office Overview dashboard provides the administrator with counters, charts and tables showing information on quarantine messages that are visible from the administrator’s hierarchy, for example the total number of messages and breakdowns by site, time and type, including message senders, recipients and release requests.
The Defender for Office Actions dashboard also provides the administrator with counters on quarantined and released emails, as well as safelink and attachment policies. In addition, quick links are provided to manage quarantined emails, safe link policies and safe attachment policies.
To customize your dashboards:
Resources have been added and are available to widgets on a dashboard where Data Source is Automate Analyzed.
For example:
Quarantine Messages, Shows diagnostic information about the Microsoft Quarantined messages,
device/msexchangeonline/QuarantineMessageQuarantine Message Staging, Shows diagnostic information about the Microsoft Quarantined Staging messages,
data/MicrosoftDefenderQuarantineMessageStaging
Quarantine Email Actions#
When synchronizing and overbuild on existing items that are in quarantine, these are moved to the relevant hierarchy node associated with the user.
Automate will sync a high volume quarantine messages using the data collection capability.
The data/DataModel called: “DataCollection” provides this lightweight collection of data from external sources.
Administrators can carry out a number or list and request actions:
View Quarantined Emails and Request Release
View Released Emails
View Release Requests
View Quarantined Emails and Request Release#
A list view of quarantined email messages visible from the current hierarchy can be inspected and instances can be selected to request the message release.
Automate provides a staging area for requests (maintained in the data model: data/MicrosoftDefenderQuarantineMessageStaging).
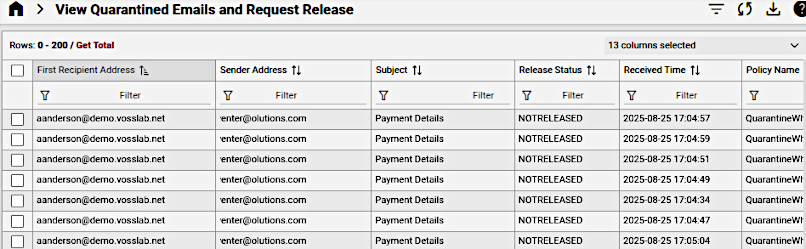
An instance from this list can be selected, inspected and managed:
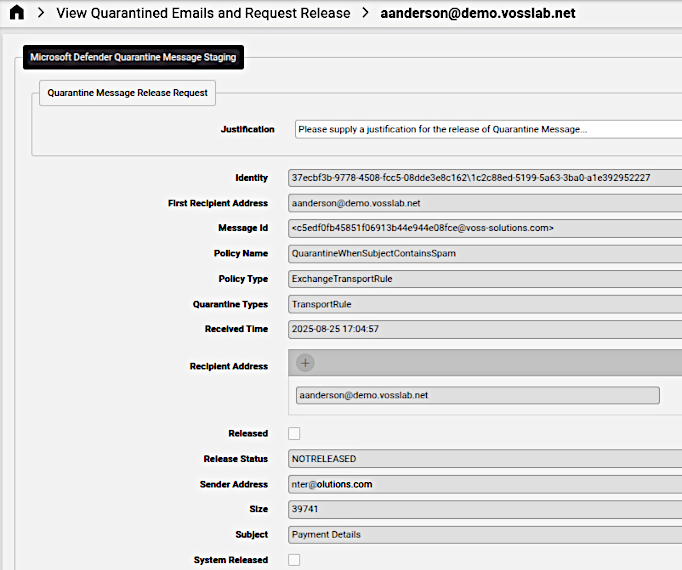
For example, administrators can select a message from this list and request the release of the quarantined email message so that it will have a State as PENDING:
Similarly rejected requests can be managed:
View Released Emails#
By default, a separate list view is available to inspect all messages that have been released from quarantine.
View Release Requests#
Following on requesting the release of quarantined messages, the requests can be listed.
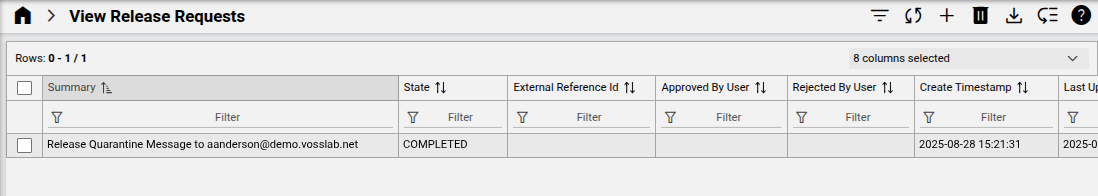
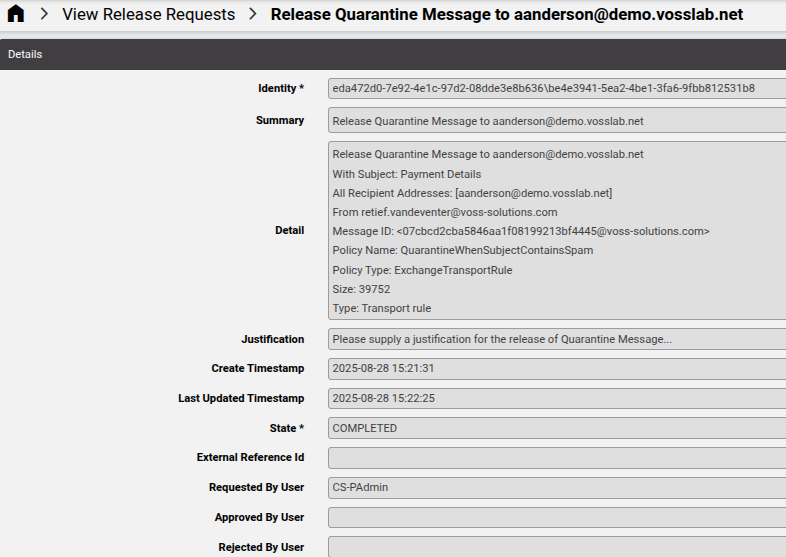
Release request instances can be inspected.
Safe Link Policies#
Manage Safe Link Policies#
Related device model: device/msexchangeonline/SafeLinksPolicy
Administrators can view and manage Safe Link policies in Automate. This includes the creation and configuration of policies.
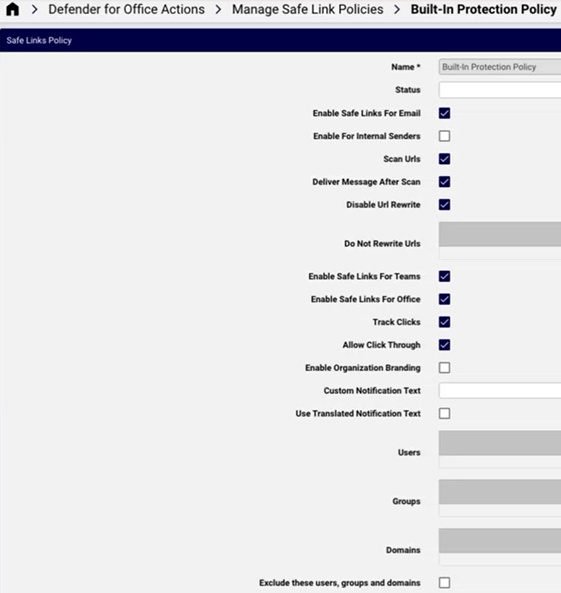
Request New Safe Link Policy#
Automate provides a staging area for requests (maintained in the data model: data/MicrosoftDefenderSafeLinksPolicyStaging).
Administrators can therefore submit requests for Safe Link policies, according to:
a selected Safe Links Policy Template
with State set as PENDING
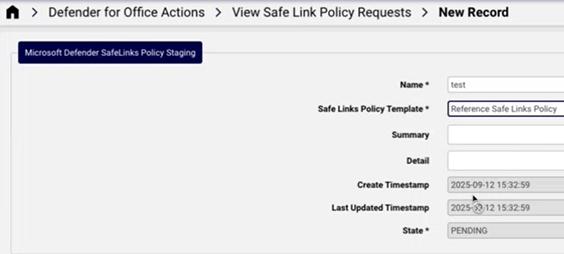
View Safe Link Policy Requests#
By default, a separate list view is available to inspect all Safe Link policy requests that have been made, and to select a request for management.
Safe Link Policy Templates#
Automate provides a reference configuration template for device/msexchangeonline/SafeLinksPolicy,
called: Reference Safe Links Policy, but administrators can clone and manage these templates according to their needs
when submitting policy requests.
Safe Attachment Policies#
Manage Safe Attachment Policies#
Related device model: device/msexchangeonline/SafeAttachmentPolicy
Safe Attachments in Microsoft Defender for Office opens attachments in a virtual environment before the messages are delivered.
Safe Attachments policies can apply to specific users, groups, or domains and can be managed in Automate.
The Quarantine policy selected when managing a safe attachement policy in Automate is managed on the Microsoft Defender portal.
The default Microsoft Defender quarantine policies are:
AdminOnlyAccessPolicy
DefaultFullAccessPolicy
DefaultFullAccessWithNotificationPolicy
NotificationEnabledPolicy (in some organizations)
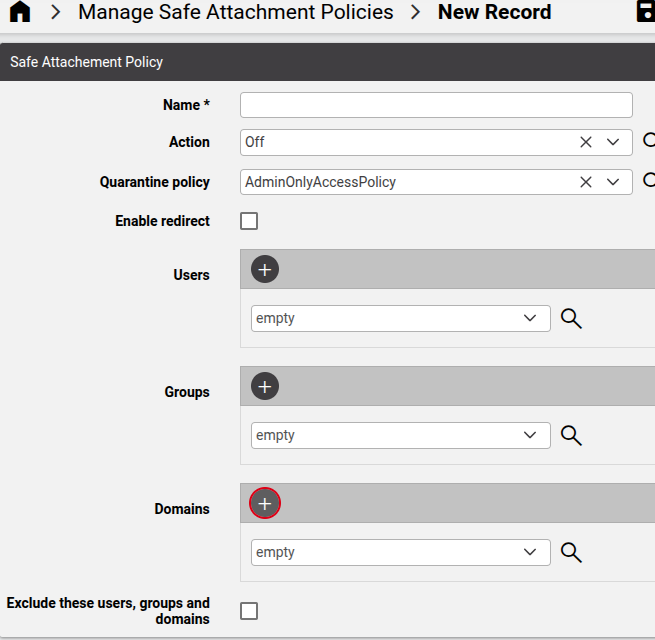
Request New Safe Attachment Policy#
Automate provides a staging area for requests (maintained in the data model: data/MicrosoftDefenderSafeAttachmentPolicyStaging).
View Safe Attachment Policy Requests#
By default, a separate list view is available to inspect all Safe Attachement policy requests that have been made, and to select a request for management.
Safe Attachment Policy Templates#
Automate provides a reference configuration template for device/msexchangeonline/SafeAttachmentPolicy,
called: Reference Safe Attachment Policy, but administrators can clone and manage these templates according to their needs.
Related Topics
Microsoft Defender for Endpoint security management and policies
Model filter criteria for Microsoft Defender Overbuild usage
