Deploy and VM Installation#
Base Install and Configuration#
This procedure installs the base system, and involves the following tasks:
Download the OVA.
Deploy the OVA.
Run the VM.
Log in as
admin.Change your password.
Configure network settings.
Download the OVA for your system to a directory accessible by the VM client.
Deploy the OVA:
Select the downloaded OVA file, and choose a VM name.
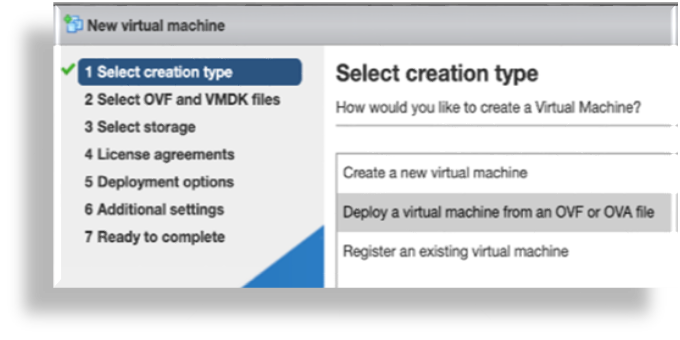
Configure storage settings via the Select storage menu, based on the recommended hardware specifications for the required configuration.
See the VMWare Specification and Requirements for your system.
Configure the network mappings based on the recommended hardware specifications for the required configuration.
See the VMWare Specification and Requirements for your system.
Run the VM, and monitor installation of the packages (this may take some time).
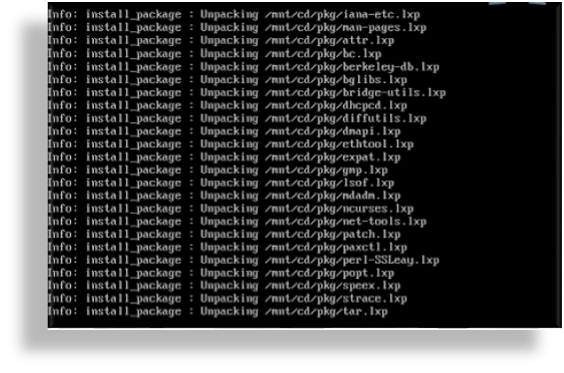
Once all packages are installed, the VM is automatically powered off, confirmed via the
auto-poweroffmessage on the console.
The system reboots. Wait until you see the About console, which displays placeholder values for hostname, version, license, days licensed and remaining, and so on.
About =============================================== Hostname: <hostname> Version: <version> Theme: <theme> Flavor: License: NNNNN-NNNNN-NNNNN-NNNNN-NNNNN Days Licensed: nnnnn Days Remaining: nnnnn Product Key: Website: <website> Kernel: Linux n.nn.nn-lxt-3 x86_64 GNU/Linux <hostname> login:
Log in:
On the About console, at <hostname> login:, log in as
admin. For the password, use the last 10 characters of the value at License, excluding the dash.Important
The License key value is only displayed on the About console. When you ssh in, it is not visible, thus, you must copy the admin password from the About console.
Once logged in, the Administration menu displays (the image displays an example for DS9):
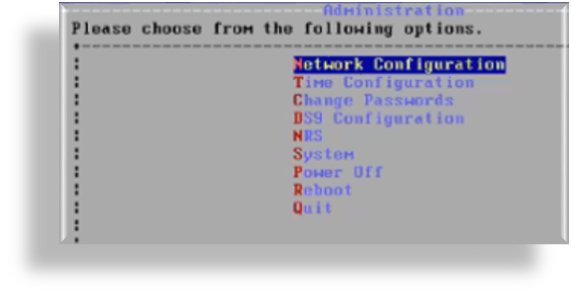
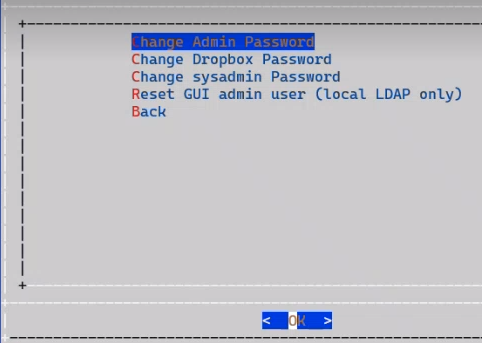
Change your password:
On the Administration menu, select Change Passwords, then change your password.
Note
It is strongly recommended that you change your password immediately.
The Reset GUI admin user option on the allows for this admin user’s password reset.
Configure network settings:
On the Administration menu, select Network Configuration.
Configure interface settings via the Interface Settings menu:
Select the relevant interface.
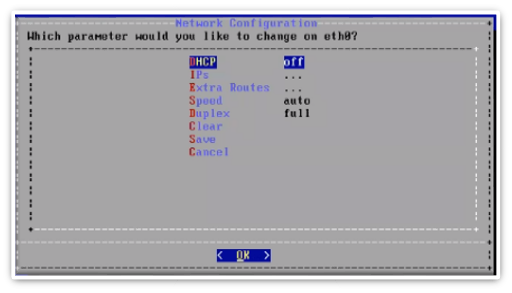
Select IPs, then set the IP address and netmask in the format
nn.nn.nn.nn/24, and save your changes.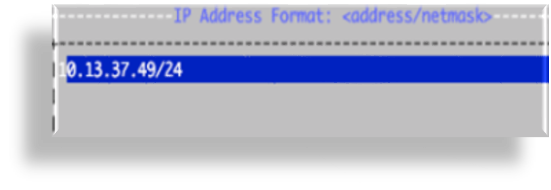
Configure the default gateway via the Extra Routes menu.

Use the following format for the entry: default <gateway IP address>
The word default is required. For additional route entries use the <subnet> < gateway> format. Similar to what would be done on a Linux system at the CLI.
Configure DNS settings via the DNS Settings menu:
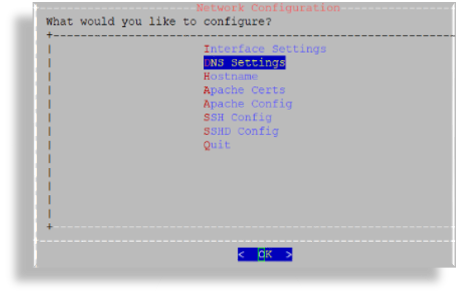
Select DNS Servers.
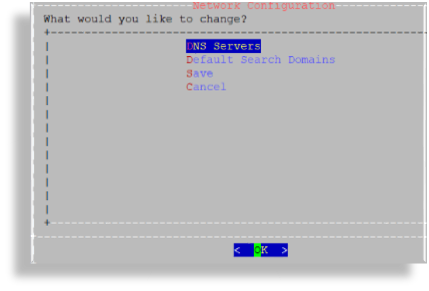
Add the IP address for each DNS server, one per line, then click OK.
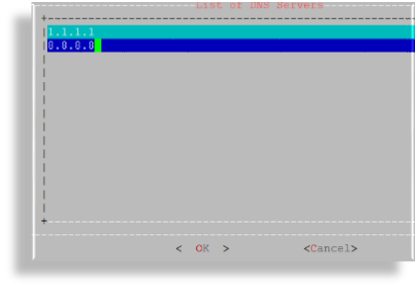
Click Save.
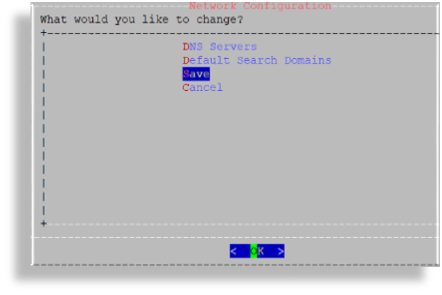
Configure the hostname via the Hostname menu, then save to trigger the update.
The console displays a message, Updating hosts. This setup may take a few minutes.
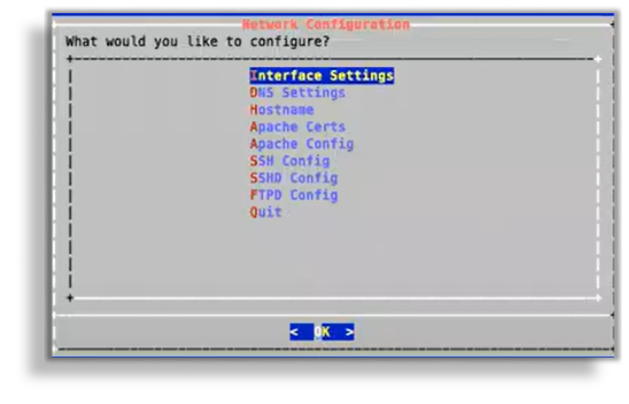
Update SSL ciphers via the Apache Config menu.
SSLCipherSuite HIGH: !MEDIUM: !ADH: !LOW
Note
SSLCipherSuitedefaults toHIGHencryption.For
SSLProtocol, only TLSv1.2 is supported.OpenLDAP defaults to
HIGHencryption.OpenSSH does not support weak ciphers.

Configure SSH settings via the SSH Config.
Custom entries can be added, if required. The following entries have been added:
kexalgorithms diffie-hellman-group14-sha1 diffie-hellman-group-exchange-sha1 hostkeyalgorithms ssh-rsa
Configure SSHD via the SSHD Config menu.
Note
Multi-line entries can be added, if required. For example, for CUCM v11.5 support, see: Multi-line CUCM Cipher Support.
This step is relevant only to an Insights Assurance solution and its integration with Cisco UC systems. This step is not relevant to the DS9 and Insights NetFlow solution.
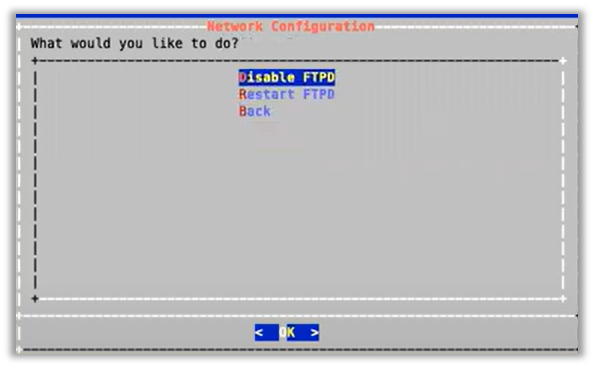
Enable/disable FTPD or restart the FTPD daemon:
On the Administration menu, select Network Configuration.
Select FTPD Config.
Important
On new installs, the FTPD daemon is disabled by default.
It is strongly recommended that the FTPD daemon remains disabled, unless there is a good reason you need to use it. It has been seen that enabling the FTPD daemon may introduce a system vulnerability.
FTPD is typically only required in rare situations, where FTP is the only way to transfer files to the server. Instead of using FTPD, it is recommended that you use the drop account with SCP or SFTP.
Base system installation is now complete. Select Quit to exit the Administration menu on the console.
Continue with product registration, and with the configuration of your system through the GUI:
Insights Dashboard
Insights Arbitrator (relevant only to an Insights Assurance solution and its integration with Cisco UC systems)
Insights DS9
Note
Prior to opening the DS9 GUI, reboot the system.
See: DS9 Product Registration and DS9 Configuration on the Dashboard
Multi-line CUCM Cipher Support#
This section provides details for the use of the SSHD Config menu option.
Note
This section is not relevant to the DS9 and Insights NetFlow solution. This solution is relevant only to an Insights Assurance solution and its integration with Cisco UC systems.
You can copy the keys into the screen in a comma separated list (without spaces).
For CUCM v11.5 support:
kexalgorithms diffie-hellman-group1-sha1,diffie-hellman-group14-sha1,diffie-hellman-group-exchange-sha1
ciphers aes128-cbc,3des-cbc,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
macs hmac-md5,hmac-sha1,hmac-sha2-256,hmac-sha1-96,hmac-md5-96
hostkeyalgorithms ssh-rsa,ssh-dss
